Modern Sourcery
These days, there is much I don't understand. I feel compelled to announce to the world my opinion on all of it.
Saturday, December 24, 2011
The Dog Was Part of It
Her name is Angel, named that way because she was all white as a pup. An Australian Shepherd from inbred parents, she was born deaf, blue-eyed, and pink around the edges.
We wanted a puppy for the kids. We didn't want to go to a puppy mill, but to get a dog no one else wanted. A deaf albino seemed a good choice to fill the billet.
She was the family dog when the kids were growing up. We let her sleep inside at first. This dog, however, was a biochemical weapon, able to release a stench so strong it could bubble paint. My father-in-law fashioned a corner of the shed for her.
We taught her American Sign Language= signs for come/dog, go, sit, stay, lay down, stand up, potty, out, toy/play, eat, speak and no. It was easier to teach her these signs than I would have thought, and it made communicating with her straightforward.
An outside dog, she always wanted to see her people. "She just wants to be part of it," we said.
She loved to run in her yard, and wore paths in the grass around the perimeter, and later, between the trees as they grew. All summer long, she would run a lap or two at top speed, then collapse into her kiddie pool, lapping at the water as she lay in it. Cooling off, the process would repeat until, her pool empty, she would find someplace cool for a nap.
She chased a squirrel into the neighbor's yard one day, so I walked the perimeter of her yard with her, telling her "No" and pounding on the ground around her boundary. As a result, I lost my wedding ring, which was a lesson for me.
She has always been there, in good times and bad, quietly filling the niche between living accessory and trusted friend.
Over the last year she's developed an intermittent cough that the veterinarians could not diagnose. After a summer filled with her usual routine, this fall she developed a limp, and lost her appetite for the brand of dog food she's enjoyed for years. We thought it was old age, and began adding liquid to her food.
The limp worsened and it was hard to watch her walk. A blood test revealed the likely culprit. She has cancer.
The poor old girl isn't eating much now, and spends most of her time sleeping. Though her eyes have dimmed, she still wants to see her people, to be part of it again for just a little while.
Monday, October 24, 2011
How Do I Get To Sleep
What follows is a direct method for getting to sleep. But first, you need to understand why you can't sleep.
If you're in physical pain and can't get comfortable, get medical advice.
If you drink coffee or caffeinated beverages during the day and can't sleep at night, stop it or cut back.
Avoid eating to excess at night, and desserts. The increase in blood sugar will keep you awake like nothing else.
Try not to use alcohol as a sleep aid. It may help you get to sleep, but you will probably wake up in a couple of hours as your body deals with its effect on your blood sugar.
With all of that, here is my direct method. It will work:
- Exercise. Some people claim that exercise at night keeps them awake, but I have found that mild exercise before bed helps me sleep. There is a balance you have to make between burning off excess blood sugar and generating too much in the way of endorphins. If you can exercise during the day, it will help your sleep. Consider calisthenics or isometrics near bed time.
In any case: stretch before bed. It helps to relax muscles and other soft tissue, and takes the edge off of excess energy. - Make a list. List all of the things you need to do tomorrow, and all of the things you are thinking about that are keeping you awake. Do not fear them; write them down. You will deal with them in the morning, when you are rested and they have been up all night worrying about you.
- Unplug. While of course you have to read the rest of this, you should put away your book, disconnect from Twitter, shut off your computer, phone, television, or other device (assuming you aren't some reader in the future who has only one device for all information sharing). These distractions are not helping you get tired to sleep, they are your excuse not to do so.
- Get comfortable. This usually means getting into bed with your own personal combination of pillows, covers, stuffed animals, or whatever. For some people this is a big deal, but for others it isn't. I don't care -- I'm just here to tell you how to sleep. I any case, you should not have to exert any effort to remain in position.
- Close your eyes. This seems silly, but how many times do people describe inability to sleep as "staring at the ceiling"? When I hear that, I always think "You're doing it wrong."
- Relax. Concentrate on your toes (individually) to make sure each one is relaxed, then your feet, ankles, and so on. Go over in your mind in whatever detail you need to make sure each part of your body is relaxed. Pay special attention to the neck and shoulders.
- Count backward. Starting at 10,000 or so, silently count slowly backward. After a while, your breathing will probably be in sync with your counting.
- You will sleep.
Monday, May 18, 2009
RealID: Not a Real ID
I am of two minds on the utility of a national ID card. As a nationalist, I like the idea of distinguishing citizen from non-citizen. But as a lover of liberty, I despise anything that extends power to the federal government. I go back and forth on this one.
But a big problem with RealID is that to obtain one a person need only supply less-secure items such as a Social Security card or State driver's license (which are often based in turn on a birth certificate plus a utility bill or two). It turns items that are easier to forge into a token that is harder to forge, and which will confer on its bearer rights he or she should not have. In security terms, it attenuates trust.
Far from combating identity theft, RealID would make it easier.
It's typical of the pattern we find for the introduction of a new product or service: make it easy to use, to spur adoption, and then play security whack-a-mole as problems are discovered.
While having a national ID card would make it easier for law enforcement officials to distinguish illegal aliens and terrorists from ordinary folks, it would not be a sufficient mechanism for doing so. Further, there is no guarantee that an ID card would be used for that purpose.
The potential for abuse, both by people obtaining false cards and by law enforcement, is staggering.
Thursday, February 26, 2009
Neal Tire and Auto of Mattoon, Illinois: Frantic Wave-Off
So it was time to get the tires rotated and oil changed. Neil Tire and Auto Service in Mattoon, Illinois assured me at the time I bought the tires that they would use the Mobil 1 full synthetic oil in my diesel Jetta. I had noticed what felt like tire balance issues at highway speed. I made an appointment for 2pm, allowing 3 hours before my next schedule item at 5pm. I thought I could get home for a while after the oil change. I mean, three hours?
So I took my lunch in to the waiting area. An older lady, well-dressed and hair coiffured, sat reading the newspaper.
Two hours in, they told me they were having trouble getting the lug nuts off. I could hear the pneumatic wrench grinding away. I wondered if I should have brought a cot. I also wondered how well they would balance the tires, since closing time was coming up and there were people waiting.
The old woman was snoring quietly in the waiting room.
After it was done, with 45 minutes left before 5pm, they told me the price, and it was $30 less than I expected. I asked what kind of oil they used. They told me they'd used Rotella. Why didn't they use synthetic? Blank look. "We always use Rotella on diesels." Realizing that the engine had had full synthetic in it since it rolled off the lot, I dropped the F-bomb. Why didn't they use Mobil 1? The clerk was polite, despite my obvious anger. Same blank look. "We always use Rotella on diesels. "
Every other place I've taken my Jetta to have the oil changed has warned me to use full synthetic.
Mobil 1 is listed on their in-store advertising, but Rotella is not.
After consultation with my wife, who's a lot tougher about stuff like this than I am, I said I wanted them to replace the oil with Mobil 1, and no, I wasn't going to pay the difference. "We always use Rotella -- I think that's good enough", he repeated with a shrug. Still, they went ahead and changed it, and didn't charge me extra.
That's the last time I get my oil changed there. I will even pay to have someone else rotate the tires I bought from Neil Tire and Auto Service in Mattoon, Illinois, because I think they're nice, but incompetent.
Saturday, July 12, 2008
I'm Selling My Comic Books
and have decided to sell them.
[I'll be updating this page regularly with listing additions and sales.
Note also the RSS feed of my eBay listings!
]
You'll be able to see which ones I have for sale at eBay.
All covers and other images are at my Picasa page.
Marvel Two-In-One (1970s) 48 books from 3-69 (ends 5:40pm CDT, July 26, 2008)
Iron Fist #15 X-Men (1977) FN/VF (
Power Man and Iron Fist (1970s) 29 books from 20-124 (
Captain America (1970s) 68 books from 178-326 (ends Jul-30-08 17:02:31 CDT)
Wednesday, March 26, 2008
Cygwin: Unix filenames from Windows filenames
#!/bin/bash
#
# sanify - turn a Windows path name into a Unix name
# - turns drive letters into /cygdrive/drive,
# - flips slashes, removes enclosing quotes,
# - replaces unusual characters with '?'
function usage() { cat <<"EOF"
Usage: $1 'Windows filename'
... where 'Windows filename' only has to be in quotes if
it has special characters, such as backslashes or spaces.
This is free.
EOF
}
function sanify() {
echo ${@} | sed \
-e 's,^[A-Za-z]:,/cygdrive/&,'\
-e 's,:,,g' \
-e 's,\\,/,g' \
-e 's,^\",,g' \
-e 's,\"$,,g' \
-e 's,[^A-Za-z0-9_\.-],\?,g'
}
if [ -t ] ; then
[ -z "$@" ] && { usage "$0" }
sanify "${@}" else
for name in `cat` ; do
sanify "${name}"
done
fi
Tuesday, February 26, 2008
A new security arms race
It won't be long before a robot will be able defeat any current Captcha system, so those with such systems deployed should make sure they A) are using multi-factor schemes for securely adding and identifying their users and B) have the latest versions of the Captcha program installed.
Since the robots are currently successful against Google only 20% of the time, there is still some time for software developers and users to stay ahead by improving Captcha and combining it with other techniques for telling humans from programs. For instance, several Captcha images could be displayed, and the user asked to identify which of them are alike, or which of them match a given pattern (also displayed via Captcha).
Tuesday, December 11, 2007
How to win on Deal or No Deal
NBC's vapid, but fun, game show Deal or No Deal seems simple enough. I doubt it will be the next Wheel of Fortune, or even the next Weakest Link, but stranger things have happened.
The contestant picks a suitcase out of 26 held up by scantily clad models. A board shows amounts, from 1 penny up to ONE MILLION DOLLARS (-oooh-). The contestant gets to pick some more, revealing the amounts held in them -- will it be ONE MILLION DOLLARS (-oooh-)? The contestant is given the choice to keep the suitcase he has, and win its contents, or go on picking others.
How to decide?
The answer is with expected value, a principle of mathematics that sounds fancy but in this case requires only simple arithmetic.
Expected value normally means finding the sum of all possible outcomes multiplied by their individual probability. It can get unwieldy, but in this simple case the odds of the outcomes are all the same, 1/N, where N is the number of values left on the board.
At any given step, add the total amount left on the board, and divide by the number of entries left. Since each amount left has equal chance of being in any of the suitcases, including your own, the expected value for a given suitcase is just the average.
When the banker calls, if your expected value if you remain in the game is higher than his offer, reject it. If his offer is higher or the same as the expected value, take it.
For instance, suppose you have entries on the board (three suitcases and your own). The amounts are $100,000, $50,000, $10, and $.01. The penny looks scary, but the $100k looks tempting. What to do?
The total is $150,010.01, which you round to $150k for an average of about $37,500. If the banker calls with an offer: $35,000, you should reject the offer. If the offer is $38,000, take it.
The reason this is the best strategy is that if you played the game many, many times, on average you'd win the expected value of what's left.
[Update: After watching this show off and on for a few months, I realized two things. First, the show did become the next Weakest Link. Secondly, simply math wasn't enough to provide a winning strategy, and in fact isn't really needed.
To win, you have to define "winning". There are two kinds of winning: winning lottery-big (a life-altering amount), and walking out with a respectable prize, one that will solve some immediate problems for you: let you open a business, buy/pay off the house, take a less stressful job, whatever.
So that gives us three kinds of numbers the cases can hold:
- Small: lower than your "respectable" win
- Respectable: At or higher than your "respectable" expectation
- Lottery: A number big enough to make your offer close to respectable.
Think about the end game: you have some small prizes and two big ones, $100,000 and $400,000. If you open a case with a small number, your offer will go up; keep going. Even if you open the $100,000 case, your offer will still not go down that much, and you can accept it with glee. Only if you choose the highest of the lottery amounts will your offer go down significantly, and you walk away with a nice paycheck.
If you reject the offer when you have only one lottery prize left, you risk coming away with nothing when you have a very easy way (at that point) to solve some problems for yourself. If you only have one big amount left on the board, make the Deal.
]
Wednesday, October 24, 2007
Exceed, Cygwin, and Terminal Server
I've been having trouble getting the combination of MS Terminal Server 2003, Hummingbird Exceed 2006, and Cygwin to work together.
Cygwin's Xfree86 doesn't work well for Terminal Server, since Cygwin's X has one global X.log file that is owned by and read-only for only one user at a time. So we use Hummingbird Exceed on the Terminal Server.
But Exceed doesn't come with xterm, ssh, etc. They expect you to use rsh, rexec, or a program you configure with their proprietary goo to connect to your remote systems. Not my style.
Background
X programs running on a remote host can display on your computer through the use of a lot of complicated technology, much of which depends on a properly set environment variable named DISPLAY. It's format is
DISPLAY=your.hostname:N.m
where "your.hostname" is either the domain name your ISP gives you, an IP address, or the special name "localhost". All computers on the Internet believe that they themselves are "localhost".
Ssh programs (either the proprietary ones from SSh, Inc., or free versions such as openssh or putty) have a wonderful feature: they can hijack data to be sent to your local computer, encrypt it, send it over their secure connection, and deliver it to your local computer for display. They do this by setting the remote DISPLAY variable to (for example) "localhost:10.0". Remote programs you run send their output to remote display 10, screen 0. Ssh receives the data, encrypts, delivers, decrypts, and sends to whatever your local DISPLAY variable says.
But I've not been able to find a Windows-based Ssh program that is able to tunnel X11 connections with remote hosts to Exceed. In the past, I've just looked at the display number in the Exceed taskbar button and set DISPLAY manually, losing the benefits of tunneling.
A little digging turned up some documentation (pdf), which says:
Ok, now I know what to do. I can grab the DISPLAY number from that file, which by the grace of Hummingbird is a text file and not more proprietary goo. Unfortunately, it's a Windows file, with an ugly filename with spaces in it. So I need a script to turn that into a Cygwin name:
While Exceed sessions are running, the display numbers are tracked through a dynamic file called Display Snapshot.HumTable. This is located in
C:\Documents and Settings\All Users\Application Data\Hummingbird\Connectivity\11.00\Global\Exceed\Display Snapshot.HumTable
As this is dynamic, it should not be edited manually.
In /etc/profile on your Terminal Server, put the following:
HUMTABLE="C:\Documents and Settings\All Users\Application \
\Data\Hummingbird\Connectivity\11.00\Global\Exceed\Display Snapshot.HumTable"
#
# sanify - turn a Windows directory name into a Unix name
# - turns drive letters into /cygdrive/drive,
# - flips slashes, removes enclosing quotes,
# - replaces unusual characters with '?'
function sanify() {
echo ${@} | sed \
-e 's,^[A-Za-z]:,/cygdrive/&,'\
-e 's,:,,g' \
-e 's,\\,/,g' \
-e 's,^\",,g' \
-e 's,\"$,,g' \
-e 's,[^A-Za-z0-9_\.-],\?,g'
}
# disp() grabs the information from the Humtable file
# and puts it in the right format.
DOMAIN=your_windows_domain
function disp() {
EX_LF="`sanify ${HUMTABLE}`"
[ -r $EX_LF ] && {
cat $EX_LF | awk -v d=$DOMAIN u=${USERNAME} \
'BEGIN {FS=","}\
$3 ~ d "." u {print "localhost:" $4 ".0";}'
}
}
export DISPLAY=`disp`
[Updated 20071026 to touch the script a bit]
Thursday, October 04, 2007
Tuesday, September 25, 2007
Script for OpenSSL Certificate Signing Request
- Generate a "Certificate Signing Request" and a key
- Send the CSR to your Certificate Authority for signing
- Wait for the signed Certificate to come back from the CA
- Put the key and the Certificate where your web, email, or other server can find them
I always have to look up the right openssl(1) command line arguments.
This year, I decided to make a script. This script takes an optional argument, the host for which you're making the certificate. I suggest generating the Certificate on the target host, but if you feel bold you can make a CSR for any host you want.
#!/bin/sh
#
#############################
#
# Shell script to automate making
# Certificate Signing Requests (CSR)
# with openssl
#
# tested on v 0.9.8e
# Loren Heal
#
#############################
echodo() {
echo "${@}"
(${@})
}
yearmon() {
date '+%Y%m%d'
}
fqdn() {
(nslookup ${1} 2>&1 || echo Name ${1}) \
| tail -3 | grep Name| sed -e 's,.*e:[ \t]*,,'
}
C=Your_Country_Abbreviation
ST=Your_State_Spelled_Out
L=Your_City
O="Your Company or Whatever"
OU="Your Office or Department or Whatever"
HOST=${1:-`hostname`}
DATE=`yearmon`
CN=`fqdn $HOST`
csr="${HOST}-${DATE}-csr.pem"
key="${HOST}-${DATE}-key.pem"
openssl req -new -newkey rsa:1024 -keyout $key \
-nodes -out $csr <<EOF
${C}
${ST}
${L}
${O}
${OU}
${CN}
$USER@${CN}
.
.
EOF
echo ""
[ -f ${csr} ] && echodo openssl req -text -noout -in ${csr}
echo ""
Thursday, September 20, 2007
Why not to buy an LCD TV
Though I'm told they do it all with mirrors.
Tuesday, September 18, 2007
Paperless Voting Logic Errors
The biggest mistake the report makes is a result of the incorrect assumption that all-electronic voting is a worthwhile goal. It fails to think outside the box created by that assumption, which would have revealed a better solution.
The report begins
Americans trust computers to run critical applications in fields such as banking, medicine, and aviation, but a growing technophobic movement believes that no computer can be trusted for electronic voting.The report could have ended with its conclusion that a computer could be trusted for electronic voting, and saved us all the trouble, but unfortunately it did not.
The fallacies fly beginning with the opening three words: "Americans trust computers" relies on an Appeal to Popularity, and Ambiguity in the words "trust" and "computers". A report intending to provide technical background and subject-matter expertise should not rely on public opinion for its primary argument. That Americans believe a certain thing does not make it true, unless we are talking about the definition of words or something else which is made true by popular acceptance. While "trust" has a variety of meanings to politicians, it has a more specific meaning in the field of computer security and information assurance. That something is trusted means only that its level of insecurity is acceptable, not that it is perfect. And the computers and most importantly the ways they are connected in banking, medicine, and aviation are markedly different than voting machines.
So the report begins by asserting that the paper trail debate is only about trusting computers, even unleashing against those who want a paper trail the ad hominem "technophobic", when in fact there is far more to it than trusting computers. It is about designing a process that doesn't require trusting computers. Many of us seeing the need for a paper trail are among the least technophobic people there are, knowing exactly when to trust a computer and when not to do so.
Most of the report sets up paper-only ballots as a sinister straw man, bringing up the history of paper ballots (e.g., with the sidebar: "How LBJ Stole and Election with Paper Ballots") and insisting that anyone opposed to direct-record electronic (DRE) voting machines must be for that kind of corruption and inefficiency.
Unfortunately, paper-based auditing trails such as these do not allow the voter to verify that the results of an election are accurate. A DRE voting machine can provide up to three different guarantees to a voter: first, that the vote was cast as intended; second, that the vote was recorded as cast; and third, that the vote was tallied as recorded.
Despite the imprecise terminology (misusing the word "vote" for "ballot"), the electronic "guarantees" provided to the voter are not worth the paper they aren't printed on. The guarantees all require trusting the system, which is exactly what we are trying to establish. This is known as "begging the question".
The report goes even further, however, and makes a misstatement of fact, saying "The third property, that the vote was tallied as recorded, is not provided by voter-verified paper audit trails." In fact it is precisely this property which a paper trail provides.
An machine which prints the official ballot and sends an electronic copy to a central location can be far more secure and trustworthy than an all-electronic one. If each voter, or a statistically important sample of them, inspects his paper ballot, then the tally of the paper ballots had better match the electronic one. The reason is this: the ballot box could be compromised, and the electronic data could be compromised, but the task of compromising them both in the same way is exceedingly difficult, equivalent to compromising everyone and everything involved. DRE systems as recommended by this report are incapable of that level of assurance.
All-electronic voting can never be as secure, and especially not as robust, possibly even as paper-only but especially not a hybrid of both. This report may have concluded that if it had not begun with its conclusion already fixed in place.
Friday, September 14, 2007
Poisoning the Well on Electronic Voting
Rep. Vernon Ehlers (R-MI)
Robert Atkinson, President of ITIF
Daniel Castro, Senior Analyst with ITIF
They've got a heavy burden of proof to lift, since it's apparent to anyone who thinks about this subject that an all-electronic system can never be trusted.
They also have to show that they were not funded, commissioned, or beholden to someone with a motivation for making electronic voting paperless. Rep. Ehlers fails that burden immediately, because as a sitting member of Congress his insight into secure electronic voting is suspect.
They may say a paper trail doesn't in itself add security, which only applies if the paper trail is done poorly.
With the long development and approval cycle of election systems, there is a gaping hole in any all-electronic system: fault exploits are developed quickly, while the systems have great inertia. An unfixable design flaw may be widely known on election day, and yet the vulneralble system will be deployed because that's how the government works.
I'll have more when they release the report.
Wednesday, August 22, 2007
Programs I Want to Write
A To Do / Project manager
A better (robust, complete, elegant) compiler language
A March Madness tournament picker
A GUI for script writing
Monday, August 06, 2007
Keeping Safe Online
(Reposted by permission from Slashdot)
There is a tendency to want the government to do something about every problem, and the hassle of online scumbaggery is no exception. Individuals (and their guardians) need to take responsibility for their own protection, and not expect either the government to protect them (which it cannot) or for faceless strangers to be kind to them, which a tiny but significant portion will not.
Each of these steps solves roughly half of the remaining problems not solved by the previous ones.
- A fool and his unarchived data are soon parted. If you want it, make an offline copy of it.
- Switch to Linux, a Mac, or Anything But Windows. Most of the following only apply if this one won't work for you.
- Switch to Mozilla Firefox.
- Buy and install a firewall box. These are very easy to set up, and will save you a ton of trouble.
- Buy and install a virus scanner.
- Download and install Lavasoft Ad-Aware or similar spyware detector, even if your virus scanner says it provides that protection.
- Don't open email with attachments you aren't expecting, or respond to spam with so much as a single click. You have been warned.
- Stay away from porn sites. They're bad for your computer.
- Stay away from online games except those you know to be crap-free.
- You don't know that any of them are crap-free.
- Don't download commercial music except from commercial vendors to whom you pay a fee. Yeah, sucks to be us. But you get what you deserve, and if you're trying to get something for nothing, you'll give something for nothing in return.
So what do you do if your kids download some game, P2P app, or other crapware-laden piece of stupidity? Take away the computer. What if you have several kids, and you don't know who did it? Enlist their aid and hold them all accountable. Tell them that if any of them downloads crapware and the guilty party won't come forward, they all do their homework at the library (for a week or month or whatever).
Saturday, August 04, 2007
A.Rod's Big Day

"The Yankees' Alex Rodriguez became the youngest player to reach 500 home runs on Saturday."
Now, I know it's not really ambiguous, since hitting 500 home runs over the course of a career is still fairly rare.
Just saying.
Oh, and congrats Alex. Maybe now you can get a decent contract and start making some real money.
Friday, August 03, 2007
Making Strings Out of Numbers in C
So I wrote itoa.c, which does the job. The file also contains a test wrapper with a main() function which may be useful in its own right. It will convert a decimal number on the command line to its representation in any base from 2 to 62.
One feature you may like or dislike is itoa's use of malloc() to get space for the resulting string. Itoa figures out how much space to allocate, which makes for twice the work for it but may save a large hassle in the calling function. I think that's an example of robustness, since it works correctly for any base, but your mileage, etc.
How do I know it works correctly for any base from 2 to 62? By inductive proof. The length for a string whose value is less than its base is 1 plus a null char for C, so the length is 2. So suppose the algorithm works for some base k. Since the same work is being done* when actually filling in the string with ritoa(), we see that working for base k means it works for base k+1. The boundary at 62 also works, so the algorithm is correct.
As always with C, be sure to garbage collect with free() when you no longer need the string.
/*
* Itoa.c
* Copyright 2004, Heal Consulting
* Published under the General Public License. See it at http://gnu.org
*/
/*
A sleeker version is available at:
http://www.cs.princeton.edu/courses/archive/fall96/cs126/examples/itoa.c
*/
#include/* only needed for main, fprintf error*/
static char *ItoaDigits =
"0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz";
/*
* ritoa
* recursive itoa
*/
long int
ritoa(long int val, long int topval, char *s, int base)
{
long int n = val / base;
if (n > 0)
topval = ritoa(n, topval, s+1, base);
else
*(s+1) = '\0';
*s = ItoaDigits[ topval % base ];
return(topval / base);
}
/*
* itoa
* - mallocs a string of the right length
* - calls ritoa to fill in the string for a given base
*/
char * itoa(long int val, int base)
{
int len;
char *s,*buf;
long int t = val;
for (len=2; t; t /= base) len++ ; /* quickie log_base */
/* printf("len; %d\n", len); */
if((buf = (char *) malloc(len)) == NULL)
{fprintf(stderr,"out of memory in itoa\n"); exit(1);}
s = buf;
if (val < 0)
{
*s++ = '-';
val = -val;
};
len = (int) ritoa(val, val, s, base);
return(buf);
}
/*
* The test program may actually be useful.
* Converts a decimal number (long int) to a base you supply.
*/
int
main(int argc, char *argv[])
{
long int num = 0;
char *s;
int base = 10;
int maxlen = strlen(ItoaDigits);
if (argc >2) { base = atoi(argv[2]); };
if (argc >1) { num = atol(argv[1]); };
if ((argc <= 1) || (base > maxlen ) || (base < 2))
{
printf("Usage:\n\n%s [number [base]]\n", argv[0]);
printf("where number is in decimal and 2 <= base <= %d\n", maxlen);
exit(1);
}
s = itoa(num, base);
puts(s);
return(0);
}
After I wrote it, I found a slightly sleeker (base 2 through 16 only) version from an old Princeton CS class*.
* No, I didn't go to Princeton. That's why I waved my hands in the proof.
Tuesday, July 31, 2007
What To Do With Old Mesh Fruit Bags

Pond filter intake cover
If you have a small garden pond with a filter and pump, a mesh bag over they intake will keep leaves, worms, and minnows out of the filter.
Wash rocks
If you have to clean decorative rocks or gravel, a mesh bag can allow you to spray a hose at the rocks without scattering them.
Big scouring pad
Fill a mesh bag with cotton rags and use as a scouring pad for a boat hull, RV, wood deck, or house exterior.
Recycling container, especially for
- aluminum cans
- glass
- tin cans
- As dust rags
- In paint preparation, to remove steel wool fibers or wood dust
Eric Wolfram, whence I stole the images here, lists several uses, including:
- Giving away at farmer's market
- Holding batteries, cables, and other electronic gear
- Carrying loose change to the bank
- Beach bag
Apparently birds get their feet caught in the modern mesh bags. Make a cube out of hardware cloth (wide-mesh heavy gauge screen) instead.
Air Clamp
Some objects that need to be clamped together for gluing cannot stand the stress of a regular clamp. You can combine a mesh bag with something like a plastic bread bag, garbage bag, or folded over piece of plastic sheeting, depending on the size, shape and strength of the objects, to make a clamp to glue them together.
- Glue the objects together
- Put the objects inside a mesh bag
- Put the mesh bag inside your air-tight container bag
- Use an aquarium air pump (or preferably something stronger) to take the air out of the bag
- Depending on the pump you have, you may either seal the bag or let it continue to try evacuating the bag.
Monday, July 30, 2007
What To Do With Old Toothbrushes
One nice feature of the humble toothbrush is that the plastic handle can be broken, either to remove the head to use just the handle, or to make the handle shorter. With gentle pressure and even low heat, the handle can also be bent into a more convenient shape. The bristles can be trimmed to form a stiffer brush or even removed entirely.
Break the handle to about 3" and use as a fingernail cleaner.
Hang in the shower for scrubbing nails and feet. Make sure to clean (and disinfect) it between uses, or various nastiness can grow on it.
If the bristles are cut off, a toothbrush can be filed down with concrete and sandpaper to a surprisingly sharp point or blade, to make an awl or a scraping tool. An old toothbrush can really come in handy in a variety of settings:
In the garage:
- General cleaner
- Clean grease, oil and tar from car parts
- Clean dirt from garden tools and apply used motor oil as protectant
- Clean rusty items
- Car detailing: either inside or out
- Bike chain and gear cleaner
- Clean power tools such as jigsaws and Sawzalls™
- Brush the dust and debris from shop vacuum cleaners
- Use as applicator for pipe thread sealant
- Spread wood glue
- Glue sand to bristles, use as wire brush
- Break and bend the handle away from the bristles to better scrub permanent coffee filters or the coffee filter basket
- Use with baking soda for general cleaning, and also the grooves in a George Foreman grill
- Clean fruits and vegetables from the garden or grocery
- Painting and paint preparation
- Ceiling fan duster
- Laundry stain scrubber
- Grout scrubber
- Doggy toothbrush
- Handle for steel wool, cotton ball, cloth
Cleaning combs and brushes, bottles, jewelry, shoes, sliding door tracks, toys, window crevices, screens, toilets, faucets, etc. [using different brushes, obviously]. Use as an eyebrow brush.
Saturday, July 28, 2007
What To Do With Used Motor Oil
Most places have laws about what you can do with used motor oil, such as mandating that it be recyeled* by a licensed facility. In fact, while writing this it was initially difficult to find any information on used motor oil other than pleas to recyele it. Used motor oil is a known carcinogen, so wear gloves and don't eat it.
A lot of the pages on the net that talk about used motor oil take the amount of oil bought and subtract the amount recycled, concluding that this amount is dumped down storm sewers or into lakes and streams. But the thing is, most people don't live near a lake or a stream, and very few people would actually dump used motor oil down the storm sewer, much less their own drain. At least, not twice.
So what do people do with used motor oil if they don't recyele it?
- Paint the bottom of wooden posts, or anything else that will be in ground contact. If you're really serious, heat the oil to above the boiling point for water and immerse your object in it. The water in the object will boil away, to be replaced by oil and contaminants. Oiled wooden fence posts that are mostly or entirely encased in concrete will not harm the environment. Don't use such posts in standing water or marsh, because the oil will leech into the water.
[Update: I found this research report from Donald J. Miller of Oregon State University, Service Life of Treated and Untreated Fence Posts: 1985 Post-Farm Report. "Post-Farm" refers to a farm full of posts, not a report after the farm.
He recommends used motor oil or crankcase oil only as a carrier for creosote, presumably because the oil only increases the useful life of posts by a short amount of time compared to its toxicity (and tendency to soften untreated wood). Using oil to carry creosote proved among the most effective treatments. In a residential or non-farm application, applied to already treated wood, plain appears to help a lot. /Update 20070728] - Soak hard-to-burn things like damp wood before lighting (don't breathe the smoke)
- Paint concrete (again, not for aquatic use).
- Paint concrete forms so they can be removed more easily taken off and reused
- Paint a brick foundation, especially the chalky mortar as a way to postpone tuck pointing. This iwill make your eventual tuck pointing job more difficult, since the new mortar will not stick as well with the oil present.
- Before paving asphalt (or asphalt over concrete), apply a coat of motor oil and allow to soak in overnight (unless rain is expected).
- Mix with staining colorants, or with old oil-based wood stain or paint. A lot of times there are things that need to be painted that will never show -- you're just painting them to protect them (why else use an oil-based paint?). So combine your leftover stain, paint, varnish, and used motor oil in a paint can and mix well. It probably won't stick to metal, but will last a long time on wood, concrete, or stone. For an effective finish, apply several coats until it is no longer absorbed.
- Use as chain saw chain oil (a very good use, but watch the splatter)
- Lubricate a bicycle chain (this is not optimal, because the thick oil tends to collect dirt)
- Clean rusty metal (paired with an abrasive such as steel wool)
- Coat outdoor tools such as axes, shovels, and clippers to keep them from rusting
- Clean road tar off vehicles (take care not to mar finish)
- Clean old engines such as on lawnmowers
- Lubricate hinges, latches, and other rough exterior hardware
- Coat nails to make them drive easier and stay rust-free
- Mix in 1 part oil with 20 parts diesel fuel and drive around †
- Oil leather (makes a dull, unattractive finish, but functions well) (do not used next to skin)
- There is a patented process for cooking used rubber tires with used motor oil, producing a variety of hydrocarbons and chemicals.
- Another (patented) process purifies used oil with acetone and ketone
- Use a centrifuge to separate impurities †
- Burn in an oil heater designed for used oil†
- Burn it in an oil lamp†
- Spread it on the ground to inhibit dust or weed growth, as this makes a nasty runoff when it eventually rains.
- Ingest it or let it contact your eyes or other such areas.
- Dump it down the drain, as this will clog your drain and mess up the sewer system
- Put it in a landfill, as this is dangerous and harmful in about six ways.
* I have left the spelling as "recyeled" to allow searchers to find this post by excluding the correctly spelled word.
† ← I've never tried these, but they should be interesting
Wednesday, July 25, 2007
How to Pull Cables with String
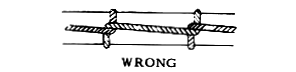
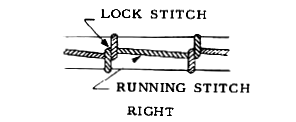
Either the "Right" or "Wrong" style will work, and I describe the "Wrong" method below. This works for Ethernet cable, Romex®, and similar cabling. It's a great technique to use with fish tape, the metallic band on a reel used to fish inside of walls.
- Make two loops in the string.
- Turn one around.
- Stick the cable through the loops.
- Pull on the string to tighten (it's OK for the loops to separate). If done properly, the harder you pull on the string, the tighter the knot gets. If done wrong ... just do it again.
- Wrap with as little electrical or duct tape as possible to secure the loose end of the string, protect your cable end, and to keep the end of the cable attached to the string so it doesn't wedge as you pull it. Too much tape will snag as you pull it through.
For fish tape, you typically fish the tape from where you want to go to where the cable is. Attach the string to the hole in the end of the tape. The other end of the string gets the procedure above.
Sometimes your intended run is such that you can't get yourself or the fish tape reel to the destination. If you have an open space between two holes, sometimes the fish tape flops around. In those cases, attach the string to the fish tape before fishing it through, so that you can control the tape a bit with tension on the string. You will then have string all the way through the run.
I've used this knot (doubled) for connecting two ropes, since other knots form a point of weakness and this one doesn't (when doubled). Knot the loose ends in a square knot rather than with tape.
What To Do With Old Wire and Cables
- Copper cable can be recycled, but finding a recycler nearby who deals with it may be difficult. Luckily, Earth911.org provides a recycler locater search box.
- Use old RG58 Ethernet cables with BNC ends as speaker cables, with BNC jacks in wall plates as needed. This type of cable is designed to carry radio frequency signals, and works even better at lower audio frequencies where impedance is negligible. It's easy to use, way cheaper (if you've got it already) than doing what this guy recommends. The sound is the same.
- Old twisted-pair (Cat-3 or Cat-5) Ethernet cable works great as a source for color-coded twist ties. Leave the vinyl jacket on until use, then strip off as much as you need. Or you can cut it all up and stand it in a jar.
- Rope: braid a strand of copper cable with two strands of other cord, of either synthetic or natural fibers. This makes a rope that is stronger than the individual cords and that will never rust.
- Rope 2: Braid twisted sets of copper wire with strands of cotton or synthetic string of similar thickness, again making a rope. Use as many individual strands as you want, up to a practical limit. You can make the twisted sets of copper wire by attaching one end of a set of wires to an electric drill and the other to something fixed in place. Twist one set of wires clockwise, the other counterclockwise. This can be done in stages without cutting the wires. Twist each section the same amount and as tightly as desired, but avoid knotting. Braid the three (or more) pieces of cable or cord together, taking care to balance the twisting directions (so the resulting cable will tend to kink less).
- Romex makes a nice pipe hanger for plumbing work, since it's flexible but stays in shape. The individual strands (solid wire only) also make excellent heavy-duty twist ties.
- PVC-coated copper makes a pretty, multicolored flame when it burns on a campfire. The smoke is toxic, of course, and so not really good for the air, but still, it's pretty.
Tuesday, July 24, 2007
What To Do With Old Wooden Pallets

If you ever take a bulk delivery on materials, you may find yourself with several wooden pallets, and not know what to do with them beside burning them or begging the garbage man to take them away. Wikipedia suggests they can be used for a number of really clever things. Here are some not-so-clever but very easily completed projects for anyone with a hammer and nails. All of these work very well because wooden pallets are made not to come apart.
Note: most inexpensive pallets are made from untreated pine or other softwood, which will ensure that the part of the pallet exposed to the ground will begin to rot soon. Rarely, you may find a pallet made from treated pine. (If you burn it, don't breathe the smoke.) It will take a few years before the compost bin falls apart, which gives you plenty of time to find more pallets. Hardwood pallets may last longer, but are often subject to a deposit.
- Make a workbench
I did it a few years ago. I had to cut one of the pallets in half for some reason, but I don't remember why. I ended up using a scrap 2x4 as a support on the back, and some masonite or fiberboard as the top.
- Make a compost bin
Just nail three pallets together in a 'C', with the deck boards facing in. They don't have to be vertical, but it makes the composting part work better. Nail in a couple of diagonal supports on top if it won't stay rigid. Just face the back toward the neighbors and fill. You'll never have to burn leaves or buy fertilizer again.
(Image from the National Wood Pallet & Container Association, under fair use) - Build a dog house
If you have a dog, even one that mostly lives inside, using three or four pallets you can make a nice, sturdy spot for your little wolf.- Lay a pallet on the ground
- Lean two more pallets together on top of the first one, with the bottom edges of the top two resting between two deck boards.
- Nail the roof-walls together, optionally using a couple of boards to make cross-pieces at the open ends.
- Secure the roof-walls to the bottom, either by nailing them directly together or by some means left to your creativity to devise
- Cover it with plywood, shingles, or any other weatherproof material so that Fido has a spot out of the rain and sun and off the ground.
- Throw in a piece of old carpet or welcome mat for that homey touch.
Monday, July 23, 2007
Troublesome Filenames
me: That looked funny at first, but I think it's ok.
A ~ (tilde) character is shell-ese for a home directory, either your own by itself or that of a given user with "~username". So when you entered "cd ~smith", it actually took you to your home directory. The /public_html/~smith thing is a real directory with a tilde as the first character of the name. You can create a directory with that name by typing
mkdir public_html/~smithThe tilde is only interpreted as a home directory when it's the first character of a directory name, and only by csh/tcsh/zsh/ksh. Shell scripts are typically interpreted by the Bourne shell (/bin/sh), which doesn't know what "~smith" means, so sometimes shell scripts will create files named like that.
Entering
cd ~smith/public_html/~smithtook me to a directory that didn't look like your home directory. I renamed public_html/~backup to public_html/backup and public_html/~smith to public_html/smith.
There are other misbehaving filenames. Usually they come about the same way the "public_html/~smith did: UNIX file systems allows filenames to contain characters that are special to some command interpreters. For example, a mistaken cut-and-paste operation can generate several spurious commands, perhaps creating files with random names. Misbehaved filenames may make it hard to work with files, even in the newer shell programs.
For instance, files beginning with a hyphen ("-") will confound some commands. If you have a file named "-h" and try to do anything to it, the usual commands such as mv, cp, or rm will interpret the name as a command line switch and tell you you're typing the command incorrectly:
~/temp me@server 8:48> ls -lThe solution is to specify a path name for the file, either an absolute path as in /usr/local/bin/--badfile, or a relative path such as "./" (dot forward-slash, meaning the current directory).
total 0
-rw-r--r-- 1 me mygroup 0 Feb 20 08:46 --help
-rw-r--r-- 1 me mygroup 0 Feb 20 08:46 -h
~/temp me@server 8:48> rm -h
rm: illegal option -- h
usage: rm [-fiRr] file ...
zsh: exit 2 rm -h
~/temp me@server 8:48> mv -h goodname
mv: illegal option -- h
mv: Insufficient arguments (1)
Usage: mv [-f] [-i] f1 f2
mv [-f] [-i] f1 ... fn d1
mv [-f] [-i] d1 d2
zsh: exit 2 mv -h goodname
~/temp me@server 8:48> rm ./-h
~/temp me@server 8:48> mv ./--help goodname
~/temp me@server 8:48> ls -l
total 0
-rw-r--r-- 1 me mygroup 0 Feb 20 08:46 goodname
Other inconvenient filenames can require a "\" (backslash) to quote characters that are special to the shell, such as "-" (hyphen), "~" (tilde), " " (space). The newer shells offering command-line completion will automatically quote the characters for you.
Advanced users may wish to apply the stream editor sed to the problem.
For a list of names of punctuation marks, I recommend the Wikipedia entry.
Sunday, July 15, 2007
Six Flags St. Louis
We got there at 9:30am, though the park opens at 10:30. There were about 20 cars ahead of us at the gate, and by the time they opened the gate to let us in the parking lot, there were at least 100 cars waiting. We parked, showed our Internet tickets to the cashier, and then waited until 10:15 at the entrance turnstyles. We made our way toward the first ride of the day, only to be stopped by park security. They held everyone back from the attractions until 10:30.
My take: either open, or don't open. Don't do it halfway. I guess it's their business, though.
While waiting for security to stop their tyranny and allow us to ride the rides, we developed a plan. Security had deputized a couple of pre-teen kids, signified with adhesive label badges. We decided that unless word came soon that we could go into the rest of the park, we would point to the ground and say "Look! A toy!", dash past the distracted kids, and quickly take over the park, allowing us to be the first to ride the rides that day. While demponstrating that move, I didn't realize that an older boy was watching me. He looked for the toy. This could work!
But while we were still laughing at the older kid for actually falling for the trick, the guards relented from their oppression, and we dashed to the first ride.
Mr. Freeze: thrilling, but too short. On the other hand, I could sit and watch the takeoff and landing for hours. We rode it twice.
Batman: Good coaster, but even though you're upside down a lot, there's no weightlessness. The line is always too long.
Ninja: Great coaster. No line, so we went through about 6 times. We found it physically tiring, because this older coaster beats you up. Still, there's lots of air time.
Screamin' Eagle: I was surprised at how much I liked this 30+ year old wooden relic. Once the biggest wooden coaster in the world, this thing is still great. The first time though, a dad was telling his 6- or 7-year-old that the boy was brave enough to ride the Screamin' Eagle. The boy wasn't sure, and whined about Mom not riding. Dad encouraged, saying "You've already been on Ninja and Batman, you can do this one!" I said if he'd been on those, this one would be a piece of cake. I turned to my own son and whispered that I was a big liar, that this was going to kill him. Buuaaa-haah-haah. Especially at the back, you get a lot of floating air time, and the 4000-foot ride is long enough to enjoy. Since it's old, it's not as popular as the newer ones, so we got to go through several times.
(The dad and kid behind us both loved it.)
The Boss: line too long, didn't ride it. Really long wooden coaster, people said it was pretty good.
Tidal Wave: This is a short little water-car ride, the entire object of which is to make a big splash. Yes, you get wet, no matter where you sit. To get really soaked, stand on the bridge overlooking the car as it splashes into the tidal pool. I wrapped my wallet in a little park map, and it stayed dry in my pocket. Wish I'd brought a Zip-lock baggie.
A word about prices: they suck. At Six Flags, everything costs way too much. $7.50 for a turkey thigh seemed like a bargain compared to the $3 bottled water, the $10 32oz sports bottle, and the other overpriced fare. And except for the turkey thigh, which I recommend, the rest of the food was crappy.
We took a bit of a tour of their water park area. Lines, crowds, and everything is $10. Rent an inner tube (required for some attractions) for $10, a locker for $10. At Holiday World / Splashin' Safari in Santa Claus, Indiana, the inner tubes are free.
At Holiday World, the rides are maintained better, the staff is friendlier, and there is free soda all day, every day. It makes for a nicer experience.
Overall, Six Flags has some nice roller coasters, but Holiday World does, too. Given the overall suckiness of Six Flags and their attitude about grabbing every last dime you have, I'll go to Holiday World next time.
(No one paid me to write this, and I'm not affiliated with any theme park or similar competitor)
Saturday, July 14, 2007
The Transformers
I took my son to see The Transformers, a big-budget motion picture version of the television cartoon version of the Hasbro toy figures that changed from trucks and planes into alien robots.
Need I say more?
How about: this was the funniest movie I've seen since Men In Black. It was an amazing artististic success visually, perfectly cast, well-acted, well-directed (as far as I can tell) and hilarious in its overreach. The robot dialogue managed to combine the chill of Darth Vader with the intellectual depth of Mr. T. Buzz Lightyear meets Small Soldiers. We both laughed hysterically.
And I want to see it again.
Tuesday, July 10, 2007
Make a Japanese Beetle Trap
Several companies sell excellent traps for the pests, including Sterling, SpringStar, and others. And they charge $5 or so for refill bags. Of course, this drops down to 50¢ in the fall, on closeout, which you then have to store the bags all winter. But you already have an endless supply of Plastic Grocery Bags (PGBs), so why should you buy more bags?
By curling the handles and the opening of the PGB inward, you can hook the bag onto the Japanese Beetle trap made by one of the nice companies listed above. Make a loop of a 6-inch piece of wire or twist-tie, girtling the bag with it to give about a 2-inch opening. If you run out of attractant, put a drop of honey (or cut flowers if you have a lot of bees around) in the bottom of the bag. The first bugs will find the nice-smelling honey, and after that the others will be attracted by the smell of other bugs. When the bag gets full (or starts to smell bad), knot it closed and let it sit in the sun to kill all of the bugs.
A Q&A from Gardens Alive doesn't speak highly of traps, but it has some great suggestions for dealing with Japanese Beetles, including ways to attract birds (who apparently eat them) and using beetle juice to repel the bugs. I don't know. We have about a dozen active bird houses around our house, and still every year I get to slaughter Japanese Beetles by the thousands.
And that beetle juice sounds fun to make.
[Update 20070810
This year, I didn't put any traps out. The difference is that the finches who live in our bird houses have found the rose bushes, and patrol them regularly. Finches love to eat Japanese Beetles! Yay!
Whether it's the finches, the lack of traps attracting them, or some downswing in the beetle population, our roses have not been hit by the beetles this year.
]
Friday, July 06, 2007
Stupid Bugs No Match for Ceiling Fan
I suppose the reflection, which flashes about 10 times per second, looks to their pitiful little bug brains to be a really exciting flashy light. It must be near a source for some beetle food, or a sexy beetle. It's sort of a beetle disco ball.
Unfortunately, the reflection also looks like it's on the ceiling, what with depth perception and mirrors and all that. So the bugs ignore the real light bulb, a perfectly usable 60-watt incandescent little number, and go for the reflection ... but they don't get there, as a fan blade knocks them to the floor, where I swat them like bugs, or squash them like bugs under the crushing force of my foam rubber Birken-nots.
Taken a step further, by shielding the real light and only showing the reflection, a nice fan-powered bug killing system could be devised.
Thursday, July 05, 2007
What To Do With Plastic Grocery Bags
- Laundry bag - for smelly or damp articles such as gym clothes, as long as you don't leave them there long enough to mildew, which is about six hours, depending on dampness. If you have a watertight bag, consider rinsing your clothes in the shower, and storing them in the bag soapy and wet (for a few hours).
- Camping in wet or snowy weather, spare socks will stay dry in the bag, and the wet pair can be stored in the same bag (use two bags if you have more than two pairs).
- Boot liner - if you don't have good boots, put a pair of grocery bags (or bread bags) over your socks. You will be amazed at how much warmer your feet stay. A drawback is that they tend to sweat.
- Dog raincoat - If you have a stupid little dog that doesn't like cold or wet weather, rip a corner of a bag and stick the dog's head through. Pull its front paws through one handle. It may be necessary to make a hole in the bag for the tail and hind legs, depending on the breed. Pull its back paws and tail through the other hole or handle, tying the handles under the belly. Be sure to leave room at the back for the place of business, should any deposits need to be made.
- Japanese Beetle trap refill -- see instructions
- Paint can cover - before opening a can of paint, poke or cut a hole bigger than the size of your brush, but smaller than the opening of your can, in a PGB. Open the can, put the bag over the top, and poke the edges of the hole you cut around inside and under the lip of the can. Used with a brush, you will keep the paint out of the rim. With practice and care, you can even pour the paint without getting any under the bag and into the rim of the can. When finished or taking a break, use up any excess around the rim and put the top back on the can, with the bag still in place. It will seal more easily and also open more easily. Take care not to rip the bag with your can opener, but drying paint will seal small tears.
- Paint tray liner and brush cover - (at least for latex paint) turn a PGB inside out (to avoid smearing the label) and cover over a paint tray. Wrap the handles around the feet of the tray at the higher end. Pour the paint onto the bag, in the tray, and use with a brush, pad, or roller. It feels a little awkward and messy at first when used with a roller, but it works just fine. The best part: between coats, or if you need to take a break, use up the excess paint and put the wet roller or brush in the painty part. Take the bag off the tray, turning it right side out, and wrap the bag around the handle of your brush or roller. It will keep even overnight if wrapped reasonably. For longer storage, seal with a twist-tie and put it in the freezer, where it will last at least a week, and probably a lot longer. When you're done, discard the bag, or even use the bag for a trash can liner for that "new house" smell.
- Icing bag - put some icing in a PGB and poke a hole in one corner. Squeeze out a bead of icing. It's not Cordon Bleu, or even Betty Crocker, but you can write "Happy Birthday" on a cake.
- Mortar/grout bag - use the same technique as for an icing bag ... but be sure to use a different bag.
- Furniture leg cover - I guess people still shampoo carpets. If you have furniture in the room, cover the legs with PGBs to keep the water and detergents from marring the finish.
- Doggie Do recovery device - I guess city folk have to pick up after their dogs (out in the sticks we use a sand rake and tray to gather it up to put in the compost). When walking the dog, use a PGB as a glove, picking up Fido's deposit off the sidewalk. Twist the bag to seal in the freshness, and continue. You can several bags for the same walk, or if bags are scarce, our Supertwist technology will allow multiple deposits to be recovered into the same bag.
Wednesday, June 27, 2007
What To Do With Old Carpet
- Unless it smells like cat:
- Insulate the dog house
- Make a cat scratch post
- Cut into strips and put it on the garden (especially if it smells like cat)
- Use it as a drop cloth for painting
- Cover or separate furniture when moving
- With bicycle hanger hooks, attach it to the eaves of a garage or shed, paint a target such as a baseball strike zone on it, and allow your aspiring young pitcher, golfer, or place kicker to practice in style. (Note: color choice may impact effectiveness.)
- Pad or protect a pickup truck bed, sides, or rails, tailgate
- Another site adds:
- Cut up carpets for use in cars as floor mats or to line the trunk.
- Cut into small circles and place under the feet of heavy furniture.
- Take camping for a doormat, or to put under sleeping bags
- Insulate your compost pile over the winter
- A commenter at yet another site suggests using it in a greenhouse (which would go as well for any other indoor/outdoor area where function outweighs beauty, such as a garage or barn)
